Gästblogg från ManageEngines blogg som förklarar den nya tekniken user and entity behavior analytics (UEBA) som använder machine learning för att upptäcka avvikande beteenden för att boosta SIEM.
Closely monitoring the behavior of a person can reveal a lot about their true intentions. Similarly, keeping a close watch on a machine’s activities can expose potential security problems. Blending security information and event management (SIEM) with user and entity behavior analytics (UEBA) can bring numerous users and devices belonging to an enterprise under surveillance. UEBA utilizes machine learning to identify anomalies in users’ activities and then present them to network administrators to take corrective actions before they turn disastrous.
“Identities can be forged, but not behavior” is the premise on which UEBA operates.
What is UEBA?
User and entity behavior analytics (UEBA) is a relatively new category of cybersecurity tools that utilize machine learning (ML) algorithms to detect abnormalities in the behavior of the users and entities that belong to an enterprise network. UEBA monitors and continuously learns from the behavior of various user accounts and devices in the network, and establishes a baseline behavioral profile for each using statistical and probability models. Following this, any action performed by a user or entity is compared with the baseline to determine if it’s normal or anomalous. Whenever an anomaly is identified, the risk score of the corresponding entity is increased, indicating to the network administrator that there’s a potential threat.
Before we dive deeper, let’s have a look at some UEBA terminologies.

UEBA observes and adapts
UEBA closely monitors the activities of each user and entity belonging to a network, and learns their mannerisms or operational patterns. Our UEBA solution works in association with SIEM solutions by using activity logs to derive insights about the normal behavior of the entities.
Risky or not risky: UEBA decides
The following figure depicts a typical day at work for George Langdon, who works as a marketing intern at ABC Corp.

As we saw earlier, when there is a deviation from expected behavior, the risk score of the entity will increase. Let’s assume that George’s system is still active past 4pm. While this could be an intruder who has gained illicit access to George’s computer, the possibility of George himself working longer hours to complete his work cannot be ruled out. If the latter is the reason for the system being accessed at an unlikely hour, increasing the risk score serves as a false alarm.
To prevent situations like these, UEBA evolves seamlessly. It learns from the entities, and is capable of altering what is considered normal behavior. In this case, UEBA will first increase George’s risk score, but keep check on his logs. As working for longer hours becomes his routine, UEBA recognizes the pattern and brings down the risk score in turn.
Advanced analytics: The brain behind UEBA
The continuous evolution of UEBA is made possible with the help of ML, both supervised and unsupervised. In supervised ML, the system is provided with a set of desirable and undesirable behaviors. When UEBA detects any undesirable behavior, it increases the risk score. Unsupervised ML for UEBA is the smarter version, which identifies typical and anomalous behaviors on its own. It employs two main statistical models, robust principal component analysis (RPCA), and Markov chains to conclude if an action is normal or not.
RPCA:
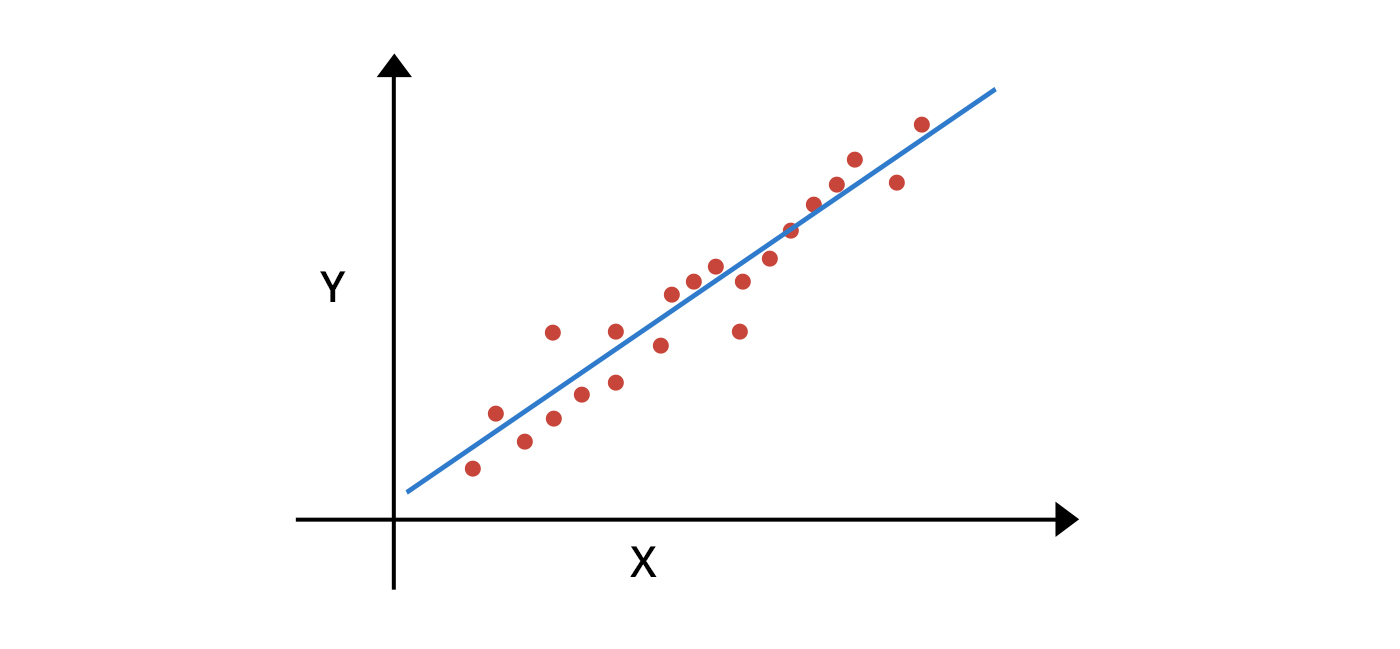
RPCA is a variation of the widely used principal component analysis (PCA) technique. It’s a statistical procedure that uses an orthogonal transformation to convert a set of observations of possibly correlated variables (data points) into linearly uncorrelated variables called principal components. The line of best fit is established for the set of principal components, and the data points that deviate from this line of best fit are termed to be anomalous.
Markov chains:
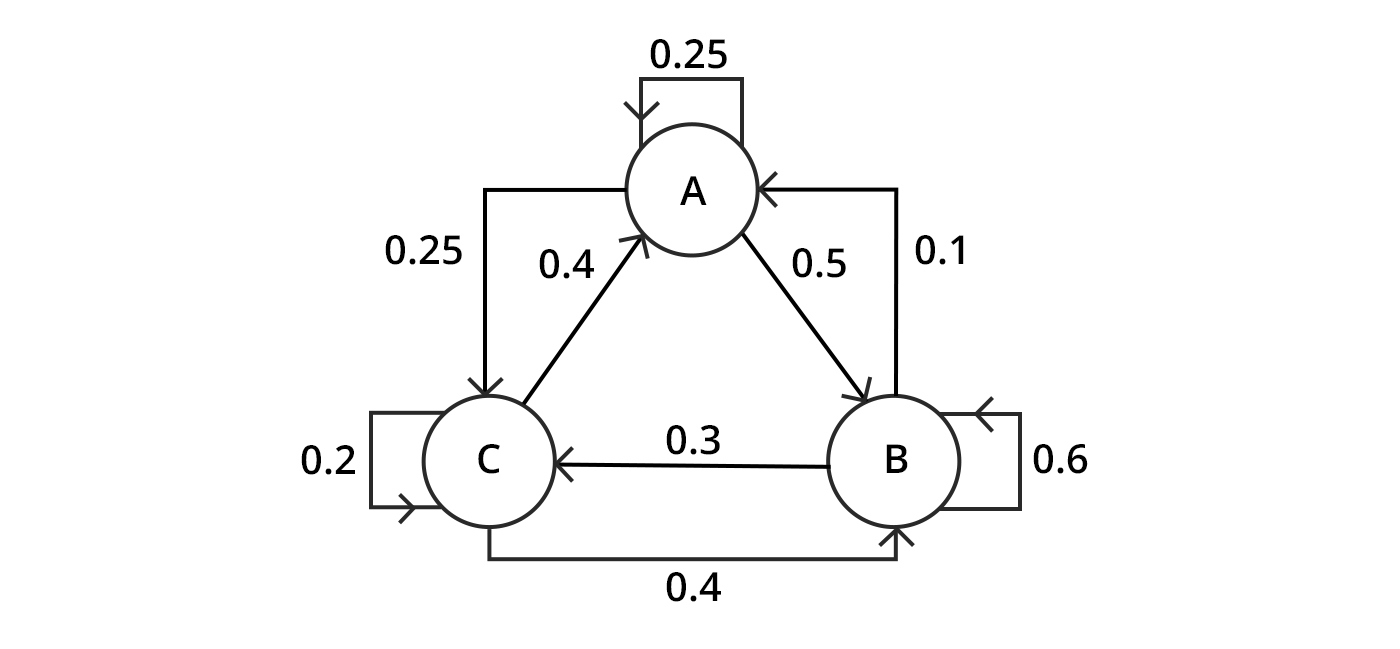
A Markov chain is defined as a sequence of stochastic events where the probability of the next event in a chain is dependent only on the state of the current event. A list is created by determining the successive state of occurrences of events. Further, as each event unfolds, it’s compared with the predicted sequence of events. If any event deviates from the probable list of events, it’s considered an anomaly, and the risk score of the corresponding entity is increased.
UEBA protects against a myriad of cyberattacks, such as brute force attacks, insider threats, lateral movement, hacking, and more.
Detecting insider threats with UEBA
It’s a busy day at the hospital. As numerous patients wait their turn at the registration counter, computers throughout the hospital freeze one by one, displaying a ransom note that demands bitcoins. In this scenario, not just the clinic’s operations but hundreds of lives could be at stake. This is an example of locker ransomware, which renders any infected device’s user interface inaccessible.

Ransomware attacks involve multiple stages: distribution, infection, staging, scanning, encryption, and payday. UEBA can detect excessive file accesses or the execution of non-native files, and then increase the risk score of the corresponding entity. This warns security personnel to take preventive measures and eliminate the attack in its early phase.
Brute-force attackers primarily target organizations with huge reserves of critical data, where user accounts are likely to have weak passwords. Higher education institutions and government departments are more likely to fall prey. Apart from disrupting the organization’s functions, the attackers can exfiltrate research files and compromise sensitive databases. UEBA can identify when a user logs in after multiple failed login attempts, or when a server access attempt is made from a remote location instead of regular access from the office. Both actions increase the risk score and serve as an indicator of a potential threat, helping to prevent an attack before the actual onset.
It is no secret that the credit card details of millions of people are available on the dark web. Data exfiltration by a bank’s own employees for monetary and vengeful motives is one of the ways in which these details end up there. Insider attacks are extremely successful and difficult to detect as the user already has permissions to access critical data. Many businesses have no clue information was stolen until it is used to execute illicit attacks.
With several data protection compliance regulations in place, such attacks don’t just tarnish the reputation of the organization involved, but can also land them in legal trouble. UEBA can be a savior in such scenarios by identifying pattern anomalies, such as an employee printing a file while the expected behavior is just adding or deleting entries in that particular file or database.
Information is a prized resource in today’s world; every organization that has valuable data is under constant threat of exposure. UEBA is an ideal watchdog that continuously learns from user actions and indicates potential threats.
To learn more, have a look at our whitepaper Understanding UEBA.
