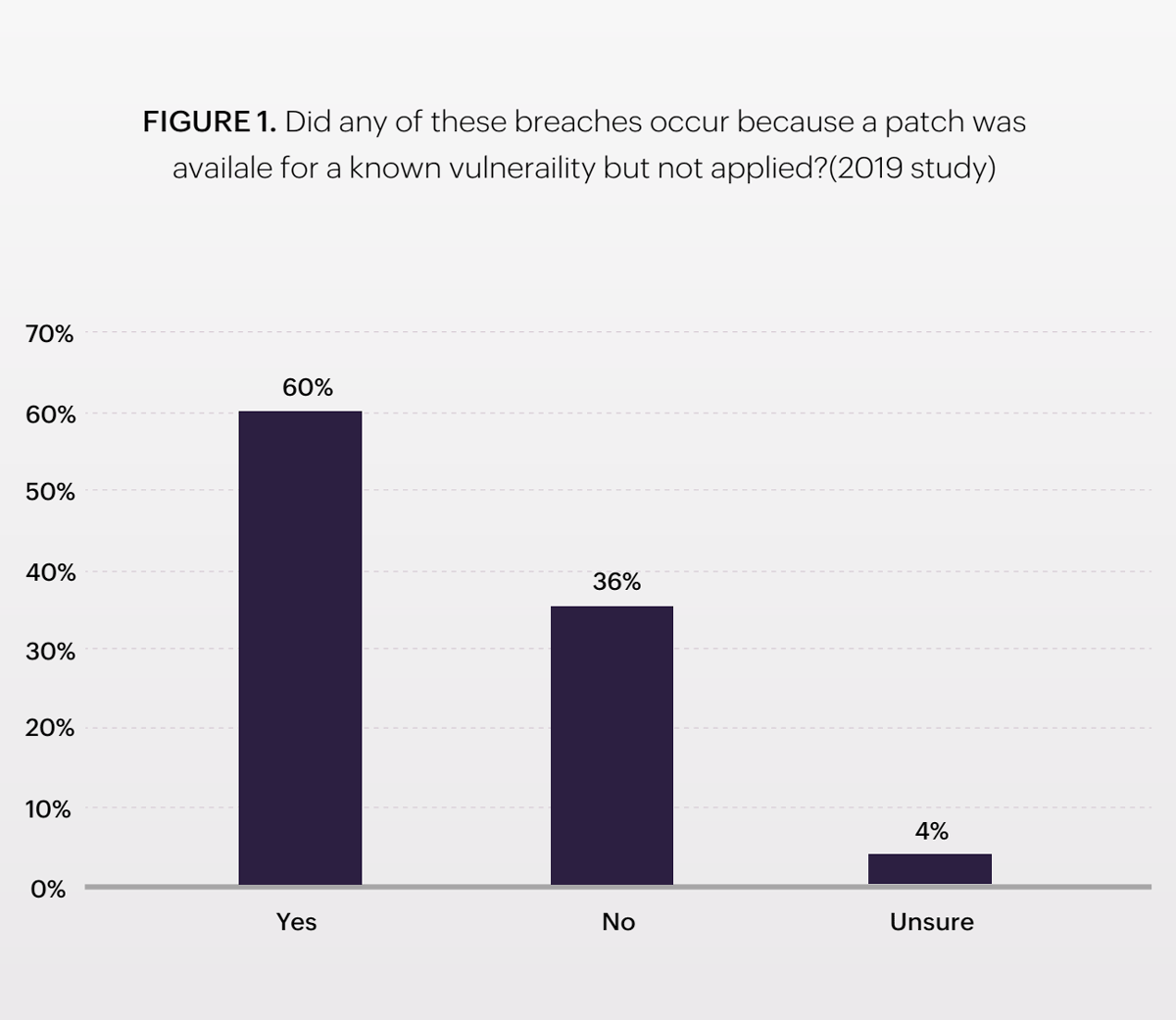In this article, we will take an in-depth look at the best practices for patch management. By following this advice, organizations can scale up their patching. In addition, we will analyze these practices to make it easier to understand.
Before we dive in, we'll provide a brief background on why the need for effective patching is so great:
In 2022, a new organization fell victim to a ransomware attack every 11 seconds. (Source: Dataprot)
A ServiceNow-funded study by the Ponemon Institute found that timely patching is critical to preventing data breaches in an organization. Furthermore, 60 percent of those surveyed in the study stated that one or more of these breaches may have occurred despite patches being available for the known vulnerabilities, but were never installed.
Best practices for patch management

Automate the patching process
Search for new patches, coordinate with teams, test and install those patches - all while not negatively impacting user productivity. Sounds like a lot, right? And imagine what it's like when all this is done manually!
The average time it takes to patch a critical vulnerability is 16 days. In fact, one of the biggest causes of delays in patching vulnerabilities is due to relying on manual processes. The longer unpatched vulnerabilities are out there, the more likely they are to be exploited by cybercriminals.
Automating patch management to ensure regular patching should be the first measure implemented in your organization for better patch management compliance.
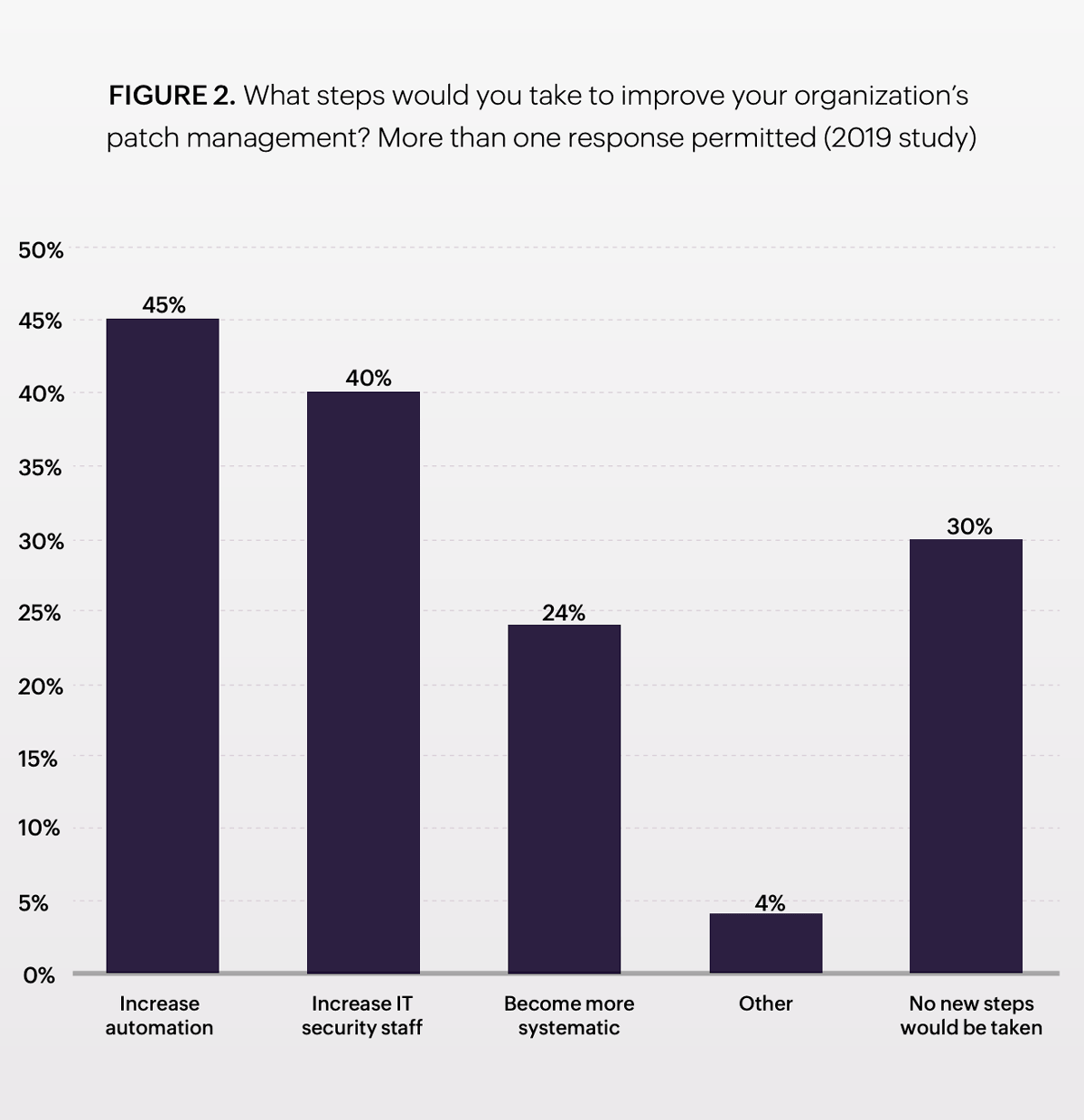
The chart above shows that 45% of survey respondents believe that increased automation can improve their organization's patch management.
Evaluate patches in a test environment before deploying them to endpoints
There are times when certain patches can affect the performance of an endpoint or even slow it down. To prevent this, it is always recommended to test patches in a pilot group of endpoints (test environment) before deploying them across the network. As a rule of thumb, your test environment should mirror your network and must consist of all the different operating systems in use.
Once patches have been tested and found to be stable, you can approve and deploy them across endpoints on the network.
Prioritize critical updates first
Prioritizing patches and highly vulnerable systems is a must to ensure patch compatibility and for effective patch management.
Recommendations when prioritizing critical updates:
- Patches with severity marked as Critical or Important should be tested and installed first
- Highly vulnerable systems* should be given high priority for patching
- Business-critical endpoints and internet-connected devices should be patched as soon as possible
- Moderate or low severity patches and less vulnerable* systems should be regularly patched according to scheduled maintenance windows
*The vulnerability of a system is defined by the number of missing patches. It varies between organizations according to their risk tolerance and patch management policies.
Schedule automatic deployments twice a week
With tens of thousands of vulnerabilities registered every year, it is imperative that you patch systems systematically. A good strategy to regulate patching is to schedule bi-weekly deployments.
Vendors release updates for products like Firefox and Chrome almost weekly to mitigate vulnerabilities. With patch deployments scheduled twice a week, you can:
- Ensure your systems are patched with all the latest updates
- Test patches thoroughly before deploying them to endpoints across the network
- Manage and monitor endpoints to check patch compliance
- Prevent slowdowns in user productivity due to shutdowns or reboots
Create configurations that fit your business needs
Creating a patch configuration that fits the entire organization's work schedule is quite a challenging task. Instead, it is better to create different groups based on domains, operating systems, specific hardware, the presence of certain applications, etc.
Here are some configurations that you can use when creating groups:
- Deployment based on Patch Tuesday schedules
- System groups based on mission-critical systems and servers
- System groups based on less critical business systems and servers
- Restart scheduling based on usage and non-working hours
Allow users to prevent interruption of business-critical activity
If patch compatibility is one side of the coin, user productivity is definitely the other and finding a good balance between the two sides is important. Allowing users to skip or delay the restart is important to ensure they are not interrupted in the middle of a business-critical task.
To ensure that patches are applied, you can either notify users to restart after a specified interval or force restart if the situation requires it.
Generate detailed patching reports
Generating detailed reports is very important for security auditing as well as for tracking patching compliance. Therefore, reports should be regularly generated indicating patch dates, version details, deployment results, and so on. As an added benefit of monitoring the patch status, you can also track the vulnerabilities being mitigated.
Patch regularly, not just for zero-day vulnerabilities
In the aforementioned Ponemon Institute study, 60 percent of organizations admitted their inability to patch a known vulnerability, which eventually caused a data breach.
As important as it is to patch quickly (zero-days), you should also make sure to have a regular patching schedule.
How to make sure patching works for staff working remotely

Secure communication between remote endpoints and the company server with an extra layer of security
Patching endpoints located in your organization's network does not pose as much of a security risk as patching endpoints remotely.
Allowing remote endpoints to connect to your organization's server for patching presents a security challenge. And it is quite obvious that such unsecured communication can lead to a plethora of security breaches.
The solution to this? Use an extra security layer that acts as an intermediary, thus preventing the organization's server from being exposed to the internet. An ideal tool would be to use a Secure Gateway Server for communication between the remote agents and the server.
Prioritize down optional updates
Prioritize installations of critical updates in remote endpoints to first confirm that they have been patched with necessary updates before rolling out less important updates.
Create separate APD tasks for remote endpoints
Creating separate automated patch deployment (APD) tasks for remote endpoints makes it easier to deploy patches. This way, you can have different requirements and configurations for these endpoints so you can actively monitor their patch compliance without any issues.
Our solutions for patch management
We work with these solutions from ManageEngine to help our customers streamline patch and vulnerability management.
Patch Manager Plus
A standalone patch management solution that fully automates the patching of Windows, Mac and Linux OS along with over 850 third-party applications. Ensure seamless patch compliance across your network with either the on-premises or cloud version.
Patch Connect Plus
Unify the management of third-party apps and updates to Microsoft Endpoint Configuration Manager (SCCM), Intune, and Endpoint Manager. With an extensive library of over 470 applications, you automate the entire patch management cycle for your endpoints.
Vulnerability Manager Plus
Assess vulnerabilities and mitigate them with automated patch management. You can also manage web server hardening, security misconfigurations, and high-risk software audits to quickly reduce your risk level.
Endpoint Central
Unified endpoint management and security capabilities that include patch and vulnerability management. A Unified Endpoint Management (UEM) solution where you manage and secure computers, servers and mobile devices. Available for on-premises and as a cloud version.
Summary
This article covered the best practices to follow when patching endpoints in your organization. By following this advice, you can improve your organization's patch management and prevent vulnerabilities in your IT environment.
If you would like to get help with your patch management or look at a tool that can facilitate your organization's patching, please contact us.